RHACS Secure Cluster Management
Install additional RHACS Secured Clusters
To monitor a cluster, you must deploy a Sensor. The following steps describe adding a sensor by using the RHACS portal
-
On the RHACS portal, navigate to Platform Configuration > Clusters.
-
Select + New Cluster.
-
Specify a name for the cluster - production
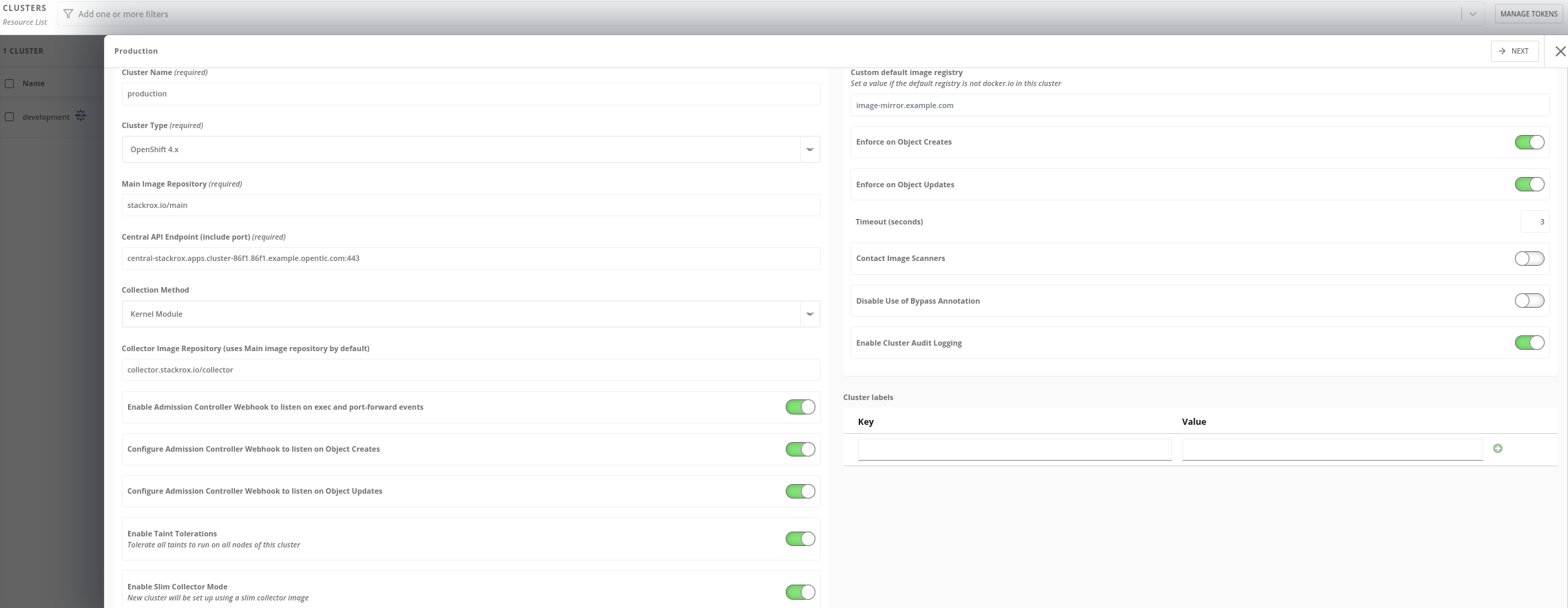
-
Click Next and download the zip:
unzip -d sensor sensor-[cluster-name].zip
./sensor/sensor.sh| the installation of the sensor will ask you to your dockerhub account, just use one dummy account if you want to avoid the integration with dockerhub registry. |
-
Once the process finished without errors, check the pods:
oc get pod -n stackroxThe pods of the admission controllers (one per master), the collectors and the sensor, will be in Running state:
NAME READY STATUS RESTARTS AGE
admission-control-6b6bcfbf48-bsldm 1/1 Running 0 80s
admission-control-6b6bcfbf48-rrppt 1/1 Running 0 80s
admission-control-6b6bcfbf48-w9wv6 1/1 Running 0 80s
collector-52jlx 2/2 Running 0 76s
collector-8pc44 2/2 Running 0 76s
collector-lgqqw 2/2 Running 0 76s
collector-qdvbq 2/2 Running 0 76s
collector-qlst8 2/2 Running 0 76s
collector-vr8h6 2/2 Running 0 76s
collector-z2frz 2/2 Running 0 76s
sensor-6b4d8447b5-bjhbz 1/1 Running 0 75soc get pod -n stackroxThe output should show oc version >=4.7:
NAME READY STATUS RESTARTS AGE
admission-control-6b6bcfbf48-bsldm 1/1 Running 0 80s
admission-control-6b6bcfbf48-rrppt 1/1 Running 0 80s
admission-control-6b6bcfbf48-w9wv6 1/1 Running 0 80s
collector-52jlx 2/2 Running 0 76s
collector-8pc44 2/2 Running 0 76s
collector-lgqqw 2/2 Running 0 76s
collector-qdvbq 2/2 Running 0 76s
collector-qlst8 2/2 Running 0 76s
collector-vr8h6 2/2 Running 0 76s
collector-z2frz 2/2 Running 0 76s
sensor-6b4d8447b5-bjhbz 1/1 Running 0 75s-
Return to the RHACS portal and check if the deployment is successful. If it’s successful, a green checkmark appears under section #2.
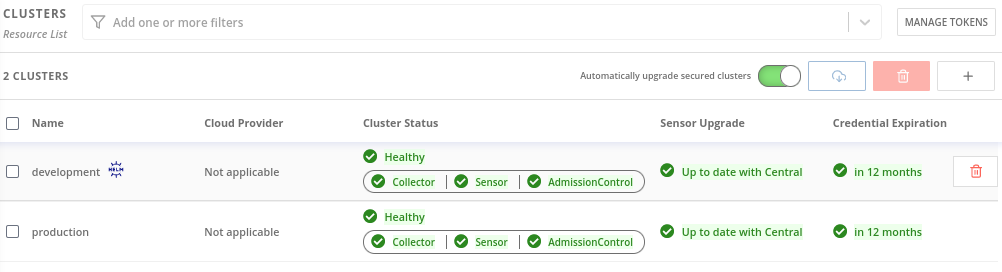
For more information check about adding Secured Clusters check the RHACS Documentation.
Add vulnerabilities to the Secured Cluster
Deploy some vulnerabilities in the new Secured Cluster added in the earlier step.
oc new-project suspicious
oc run shell --labels=app=shellshock,team=test-team --image=vulnerables/cve-2014-6271 -n suspicious
oc run samba --labels=app=rce --image=vulnerables/cve-2017-7494 -n suspicious
oc run phpunit --labels=app=phpunit --image=vulhub/phpunit:5.6.2 -n suspicious
oc run couchdb --labels=app=couchdb --image=vulhub/couchdb:1.6.0 -n suspiciousRHACS System Configuration
Check into the official documentation the different configuration tweaks that you can do in the RHACS cluster:
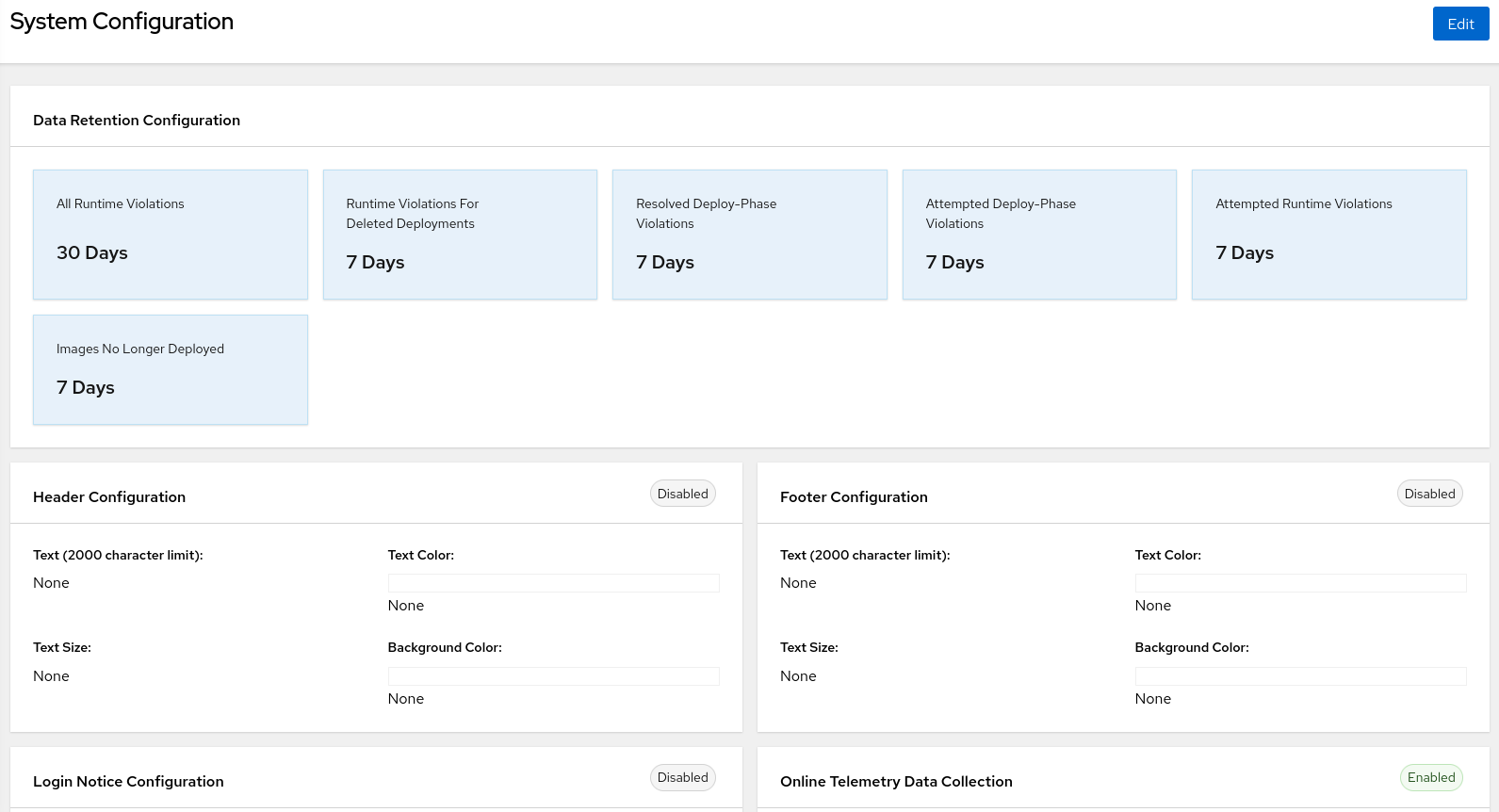
The options are:
-
Header Configuration
-
Footer Configuration
-
Login Notice Configuration
-
Online Telemetry Data Collection
RHACS System Health
The Red Hat Advanced Cluster Security for Kubernetes system health dashboard provides a single interface for viewing health related information about Red Hat Advanced Cluster Security for Kubernetes components.
To access the health dashboard:
-
On the RHACS portal, navigate to Platform Configuration → System Health.
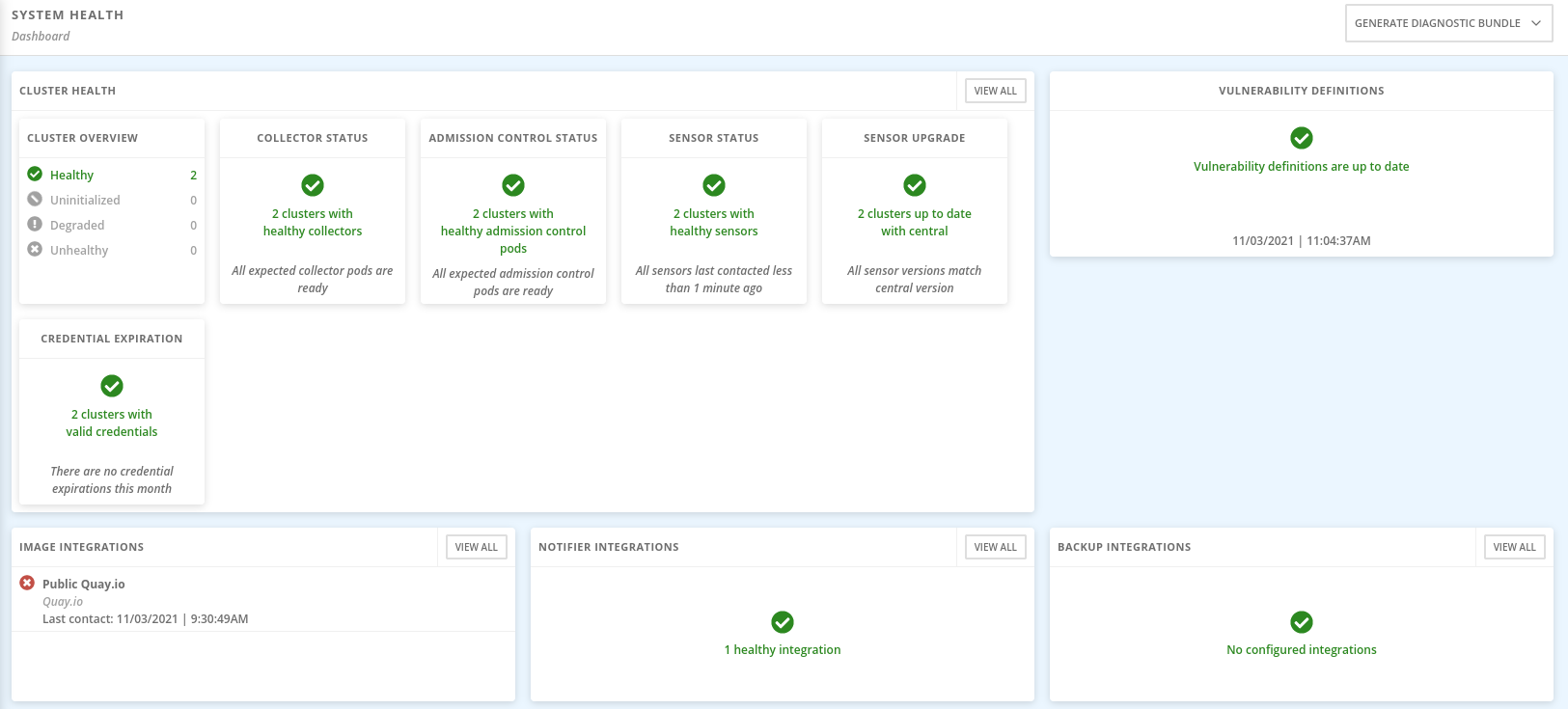
The health dashboard organizes information in the following groups:
-
Cluster Health - Shows the overall state of Red Hat Advanced Cluster Security for Kubernetes cluster.
-
Vulnerability Definitions - Shows the last update time of vulnerability definitions.
-
Image Integrations - Shows the health of all registries that you have integrated.
-
Notifier Integrations - Shows the health of any notifiers (Slack, email, Jira, or other similar integrations) that you have integrated.
-
Backup Integrations - Shows the health of any backup providers that you have integrated.
The dashboard lists the following states for different components:
-
Healthy - The component is functional.
-
Degraded - The component is partially unhealthy. This state means the cluster is functional, but some components are unhealthy and require attention.
-
Unhealthy - This component is not healthy and requires immediate attention.
-
Uninitialized - The component has not yet reported back to Central to have its health assessed. An uninitialized state may sometimes require attention, but often components report back the health status after a few minutes or when the integration is used.
The Cluster Overview shows information about your Red Hat Advanced Cluster Security for Kubernetes cluster health. It reports the health information about the following:
-
Collector Status - It shows whether the Collector pod that Red Hat Advanced Cluster Security for Kubernetes uses is reporting healthy.
-
Sensor Status - It shows whether the Sensor pod that Red Hat Advanced Cluster Security for Kubernetes uses is reporting healthy.
-
Sensor Upgrade - It shows whether the Sensor is running the correct version when compared with Central.
-
Credential Expiration - It shows if the credentials for Red Hat Advanced Cluster Security for Kubernetes are nearing expiration.
RHACS Access Control
Red Hat Advanced Cluster Security for Kubernetes (RHACS) comes with role-based access control (RBAC) that you can use to configure roles and grant various levels of access to Red Hat Advanced Cluster Security for Kubernetes for different users.
Red Hat Advanced Cluster Security for Kubernetes 3.63 includes a scoped access control feature that enables you to configure fine-grained and specific sets of permissions that define how a given Red Hat Advanced Cluster Security for Kubernetes user or a group of users can interact with Red Hat Advanced Cluster Security for Kubernetes, which resources they can access, and which actions they can perform.
-
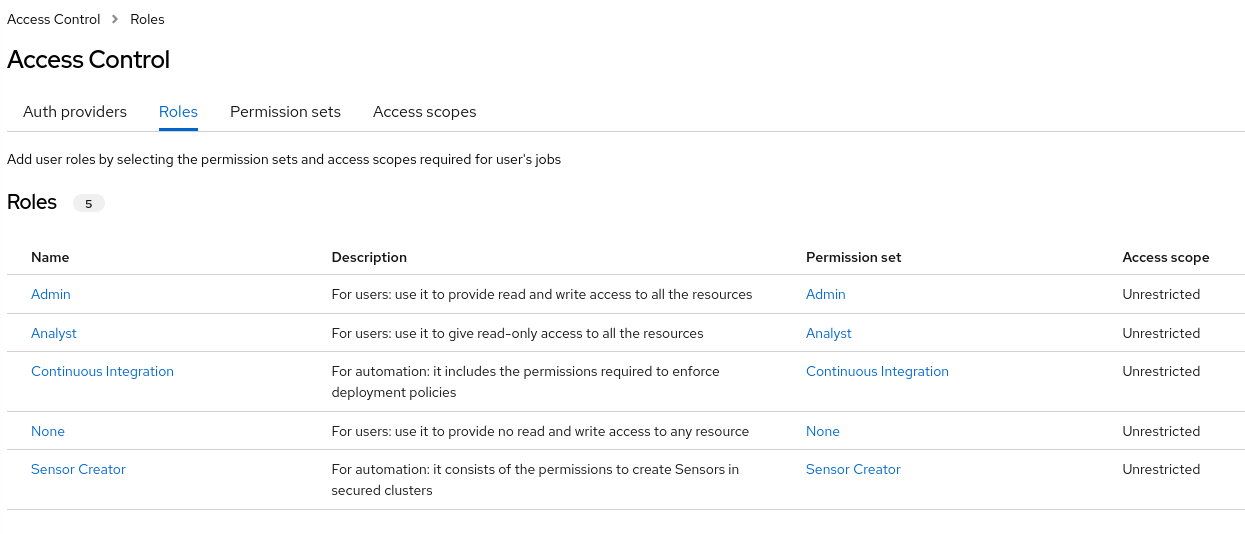
Roles are a collection of permission sets and access scopes. You can assign roles to users and groups by specifying rules. You can configure these rules when you configure an authentication provider. There are two types of roles in Red Hat Advanced Cluster Security for Kubernetes:
-
System roles that are created by Red Hat and cannot be changed.
-
Custom roles, which Red Hat Advanced Cluster Security for Kubernetes administrators can create and change at any time.
-
-
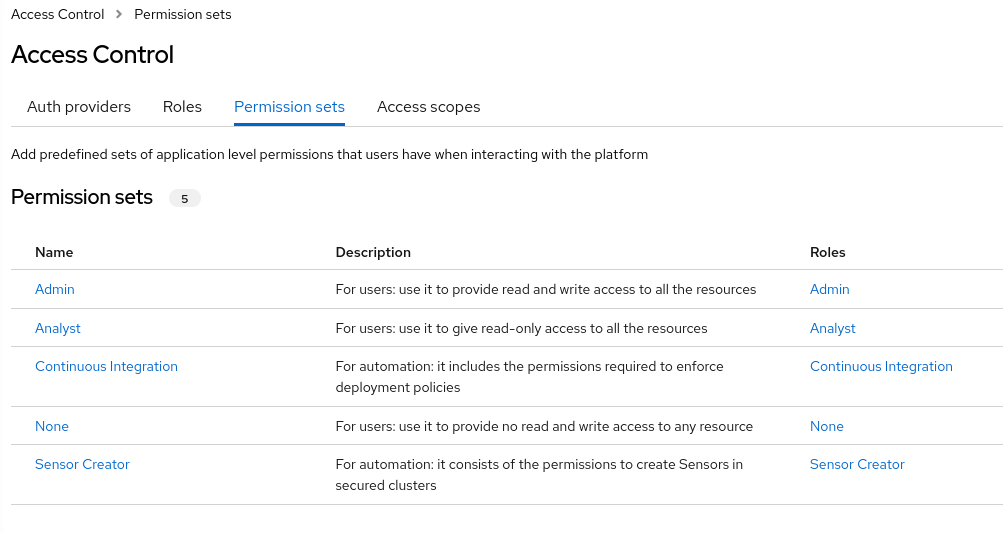
Permission sets are a set of permissions that define what actions a role can perform on a given resource. Resources are the functionalities of Red Hat Advanced Cluster Security for Kubernetes for which you can set view (read) and modify (write) permissions. There are two types of permission sets in Red Hat Advanced Cluster Security for Kubernetes:
-
System permission sets, which are created by Red Hat and cannot be changed.
-
Custom permission sets, which Red Hat Advanced Cluster Security for Kubernetes administrators can create and change at any time.
-
-
Access scopes are a set of Kubernetes and OpenShift Container Platform resources that users can access. For example, you can define an access scope that only allows users to access information about pods in a given project. There are two types of access scopes in Red Hat Advanced Cluster Security for Kubernetes:
-
System access scopes, which are created by Red Hat and cannot be changed.
-
Custom access scopes, which Red Hat Advanced Cluster Security for Kubernetes administrators can create and change at any time.
-
For more information about RBAC and the integration with third parties for User Access