Overview RHACS
In this section we will face the following:
-
How to deploy ACS.
-
ACS Architecture.
-
The ACS Dashboard.
RHACS Architecture
The StackRox Kubernetes Security Platform installs as a set of pods in your Kubernetes or OpenShift cluster and includes the following components:
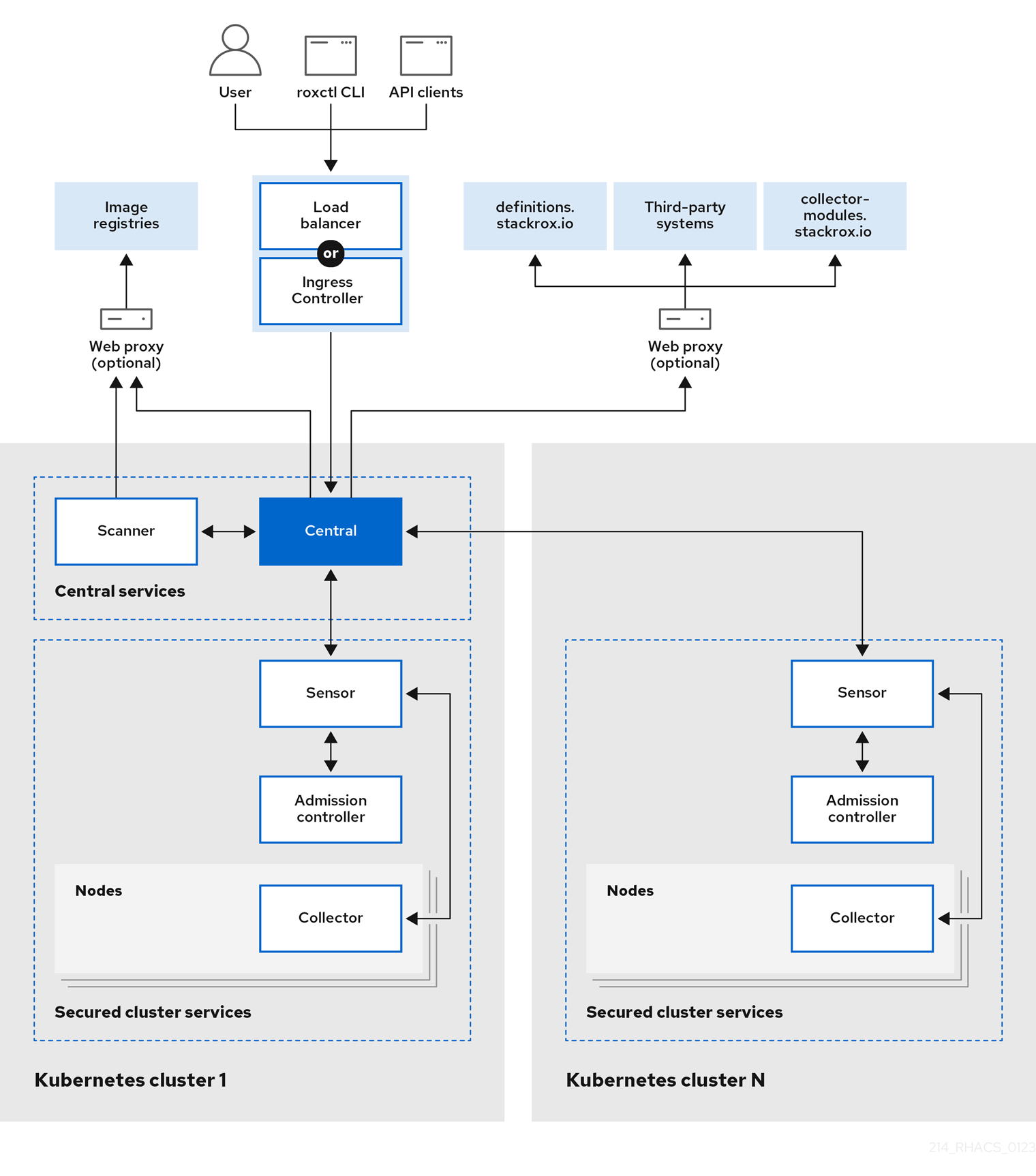
-
Central: [Centralized components] Central is the main component of Red Hat Advanced Cluster Security for Kubernetes and it is installed as a Kubernetes deployment. It handles data persistence, API interactions, and user interface (Portal) access. You can use the same Central instance to secure multiple OpenShift Container Platform or Kubernetes clusters.
-
Scanner: [Centralized component] Red Hat Advanced Cluster Security for Kubernetes includes an image vulnerability scanning component called Scanner. It analyzes all image layers to check for known vulnerabilities from the Common Vulnerabilities and Exposures (CVEs) list. Scanner also identifies vulnerabilities in packages installed by package managers and in dependencies for multiple programming languages.
-
Sensor: [1 x Per Cluster] Red Hat Advanced Cluster Security for Kubernetes uses the Sensor component to monitor Kubernetes and OpenShift Container Platform clusters. It handles interactions with the OpenShift Container Platform or Kubernetes API server for policy detection and enforcement, and it coordinates with Collector.
-
Admission controller: [1 x Cluster] The admission controller prevents users from creating workloads that violate security policies in Red Hat Advanced Cluster Security for Kubernetes. [1 x Admission Controller]
-
Collector: [1 x Node OCP/K8s Nodes] Collector collects and monitors information about container runtime and network activity. It then sends the collected information to Sensor.
| Scanner only scans those images that are not already scanned by other integrated vulnerability scanners. It means that if you have integrated Red Hat Advanced Cluster Security for Kubernetes with other vulnerability scanners, Scanner checks and uses the scanning results from the integrated scanner if available. |
RHACS Dashboard
When login in RHACS we will get the RHACS Dashboard:
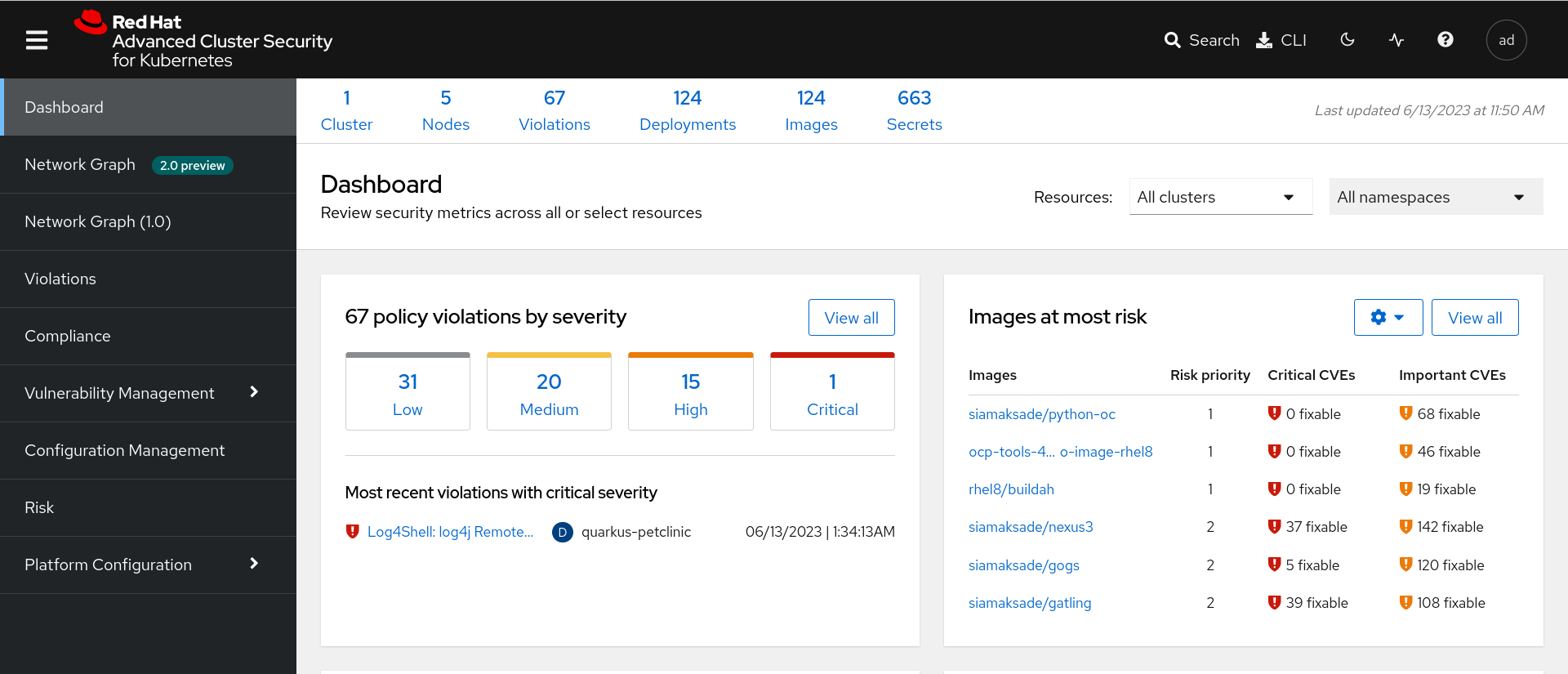
In the RHACS Dashboard we have three main sections:
-
The header.
-
The menu.
-
The information.
Dashboard Left Menu
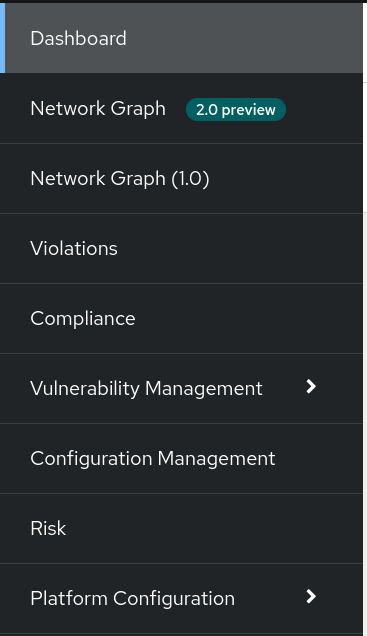
| Network Graph (1.0) will be deprecated and will be replaced by the Network Graph 2.0 version which is included as a Technology Preview. |
In the left part of the dashboard we can see the different sections we can access in RHACS to gather information about the security in the clusters we have configured in RHACS.
Later we will go deeper in each of them. For the time being, we will introduce each of these:
-
Dashboard, where we are in this moment. We can get a summarize vision of our environment.
-
Network Graph, we can get information about the configured network flows and the real ones. We can use to create Network Policies to implement network segmentation.
-
Violations, we can get all the events that do not match the defined security policies.
-
Compliance, we can get the compliance of out environment according to several indistry and regulatory security standards such as PCI DSS.
-
Vulnerability Management, get information about known vulnerabilities which are affecting your environment. Not only deployed workloads but infrastructure as well.
-
Configuration Management, review configuration to prevent possible misconfigurations which can lead to security issues.
-
Risk, review risks affecting your environment such as suspicious executions.
-
Platform Configuration, ACS configuration and integrations.
Dashboard Information
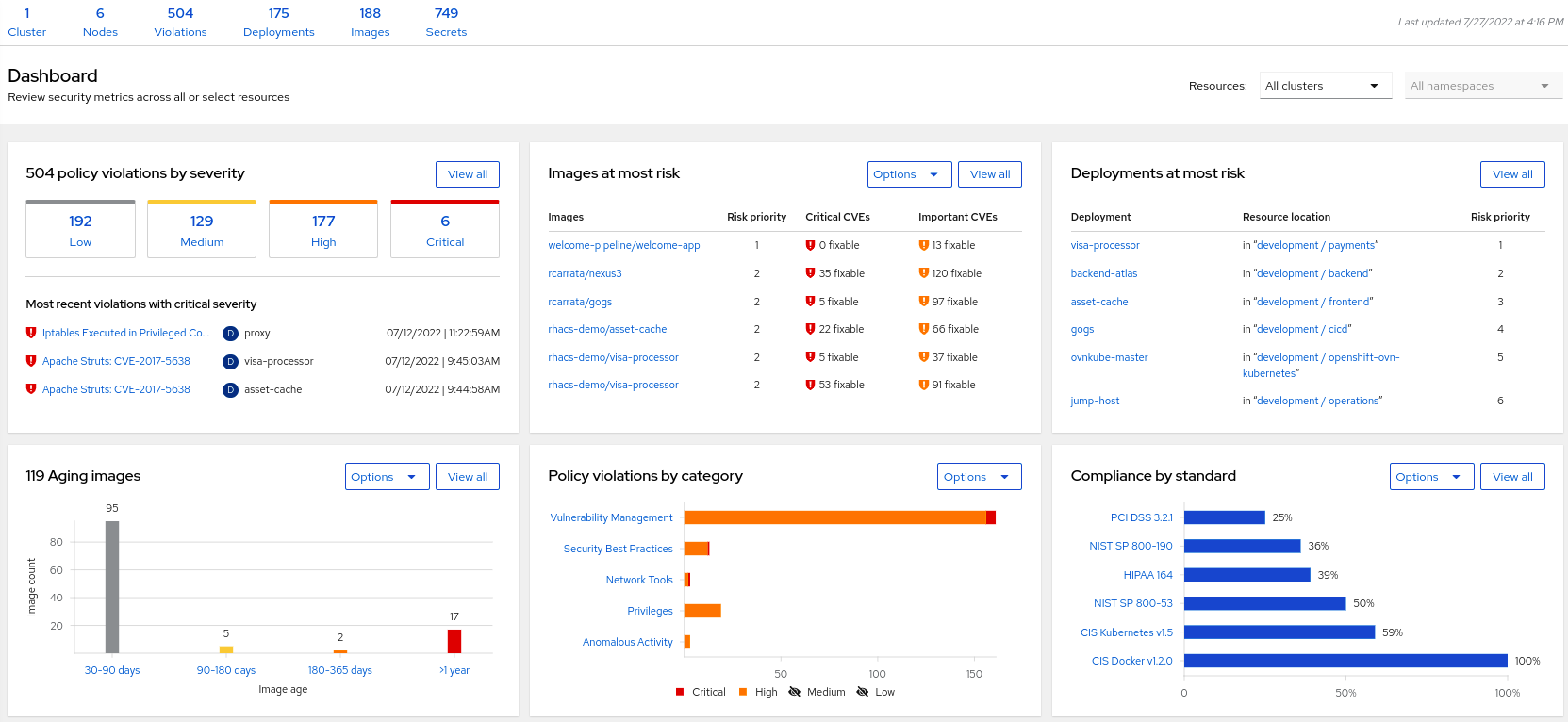
We can get a summary about the security state of the whole environment.
You can browse and click in each part to get more information.
You can spend a time browsing the information in Dashboard to get familiarized to. In the following sections we will go deeper in each one of them.
